By Namrata Sengupta, CDI member representative from BitRaser
Enterprise data is growing at a phenomenal rate that requires going above and beyond the limits of traditional storage architecture, demanding more scalability, performance, and a cost-effective storage solution. This surge has further led to the adoption of high-density, lower-cost technology-based drives such as Shingled Magnetic Recording (SMR), which delivers significantly greater areal density than traditional CMR (Conventional Magnetic Recording) drives. SMR drive is a storage technology that increases the areal density of hard drives, allowing more data to be stored per square inch of the platter. This higher density is achieved by altering how tracks are written on the disk. Unlike traditional CMR drives, where tracks sit side by side with clear separation and can be rewritten independently, SMR writes each track so that it partially overlaps the one before it, much like shingles on a roof (See Image 1).
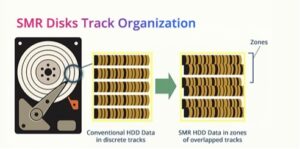
Image 1: SMR Drive Track Organization (Source: bitraser.com)
In short, SMR drives use ‘overlapping recording tracks,’ a design that boosts capacity but forces them to use sequential writes and Read-Modify-Write operations. The design, therefore:
- Narrows the width of the write track
- Allows subsequent tracks to overlap and
- Packs more tracks into the same physical area
The result is a substantial capacity boost, enabling manufacturers like Western Digital to deliver multi-terabyte SMR (up to 32TB) drives as of 2025 at a lower cost than equivalent CMR models. Some other notable SMR drives are:
| Brand | Max SMR Capacity | Notable Models |
| Western Digital | 32TB | Ultrastar DC HC690 UltraSMR |
| Seagate | 30TB | Exos/HAMR-based models |
| Toshiba | 28TB | Mx11 (MA11) series |
Additionally, SMR drives are divided into zones, and each zone must be rewritten sequentially. Because of this architecture, SMR drives follow a Read-Modify-Write (RMW) process as mentioned earlier. In order to update a small amount of data, an SMR drive may need to:
- Read the entire zone
- Modify the required portion
- Rewrite the entire zone sequentially
These SMR drives are widely used in:
- Cloud and Hyperscale environments
- Content Delivery Networks
- AI/ML Training Database
- Enterprise archival systems, including tape replacement archival environments
- Backup repositories
- Log, telemetry, and IoT/surveillance data
Data Wiping on SMR Drives Using Overwriting Technique
The Read-Modify-Write behavior of SMR drives is the core reason overwrite-based data wiping methods fail to securely sanitize SMR drives. Since logical writes do not correspond directly to physical sectors, an overwrite operation cannot guarantee that the original data’s physical locations have been overwritten. As a result, overwriting operations cannot guarantee that the underlying physical data has been overwritten, leaving residual data traces behind. Traditional overwrite methods, such as US DoD 5220.22-M (3-Pass), NIST SP 800-88 Clear (1 or multiple passes), and IEEE 2883 Clear (1 pass), worked reliably well on older CMR drives because they assumed that a logical overwrite to a specific LBA (Logical Block Address) directly overwrote the corresponding physical sector. On modern SMR drives, however, this assumption no longer holds. The drive’s reliance on Read-Modify-Write and shingled tracks breaks the fundamental premise on which overwrite-based data sanitization was built. Let us understand in detail why overwriting fails on SMR drives:
- Logical overwrites do not map accurately to physical locations on SMR drives. Drive-managed SMR abstracts its internal zone layout from the host. As a result, when an overwrite tool writes to a logical block, the drive may:
- Redirect the write to a different physical zone
- Stage writes in media cache
- Reorganize or move data internally
- Rewrite entire zones in bulk instead of individual sectors
- Delay physical rewriting until internal garbage-collection cycles
Because of these behaviors, a pattern written to a specific LBA does not guarantee that the corresponding magnetic region is physically overwritten in a direct one-to-one manner.
- Overlapping tracks make direct sector replacement impractical at the physical layer. SMR increases capacity by partially overlapping tracks. This architecture means:
- Updating a single track requires rewriting several adjacent tracks
- Performing a large RMW operation internally on the drive
- Portions of the zone may not be rewritten immediately
- Residual data may remain in not-yet-rewritten portions of zones
Overwrite standards were designed with drives in mind, where sector-level overwrites were assumed to map relatively directly to physical locations. On SMR drives, this assumption breaks down because sector writes are implemented via zone-level translation and RMW.
Note: In layman’s terms, the SMR drive often puts the new data into a temporary buffer and reorganizes it later, sometimes hours later, when the system is idle.
- Multi-pass overwriting adds no reliability to SMR drives. Legacy standards often prescribe multiple overwrite passes for added assurance. However, on SMR drives:
- Multi-pass overwrite still operates on LBAs
- Zone-level rewriting may remain incomplete across passes
- Residual data may persist inside overlapped tracks or deferred rewrite areas
Thus, an additional number of passes cannot guarantee that all original data has been physically overwritten on SMR media.
Solution For Wiping SMR Drives: Use Purge Sanitization Methods by NIST or IEEE
Given the inherent inefficiencies of overwriting on SMR drives, enterprises should rely on purge-level sanitization methods to ensure complete and verifiable data erasure. According to NIST SP 800-88 Media Sanitization Guidelines Rev. 2, Purge refers to “sanitization techniques that apply physical or logical methods to make the recovery of target data infeasible using state-of-the-art laboratory techniques, while preserving the ISM in a potentially reusable state.”
Likewise, according to IEEE 2883:2022, “The purge sanitization method uses logical techniques or physical techniques that make recovery of target data infeasible using state-of-the-art laboratory techniques applied to an intact or a disassembled storage device but that preserves the storage media and the storage device in a potentially reusable state.”
Purge methods like Secure Erase, Cryptographic Erase, and the SCSI Sanitize command bypass the architectural limitations of SMR drives. They operate inside the drive firmware, where the actual knowledge of zones, track boundaries, and caches resides. Unlike overwrite-based Clear methods that attempt to issue LBA rewrites, Purge techniques directly affect the controller, media encryption keys, or firmware-managed mapping tables to ensure all remnants of data are eliminated.
Firmware Purge commands like Secure Erase are supported by SMR drives and are executed inside the drive firmware, meaning they are aware of SMR zones, bypass logical-write translation layers, operate directly at the physical level, and perform zone-by-zone purging to ensure the underlying magnetic representation is fully cleared.
Cryptographic Erase, on the other hand, works by destroying the Media Encryption Key (MEK), instantly rendering all data unreadable ciphertext and eliminating the need for any physical overwriting. Additionally, Purge-level methods avoid all the uncertainty introduced by SMR’s read-modify-write behavior, persistent write caches, and delayed zone rewrites. Since they work at the controller layer, they sanitize the entire addressable media that include hidden areas the host cannot access. This makes Purge the only reliable and audit-ready sanitization approach for modern high-capacity SMR drives.
Conclusion: Use SMR-Aware Data Wiping Software
With the limitations of predominantly used overwriting methods like US DoD 5220 and NIST 800-88 Clear, there is a need for an intelligent SMR-aware data wiping application that can auto-detect the SMR drive and ensure that the Purge method is applied, despite the user selecting any overwriting standard for compliance reasons. It is important to note that the SMR drive is not identifiable by virtue of its design or label, and technicians are bound to make mistakes identifying it; hence, software that identify automatically an SMR drive and performs Purge techniques are advisable.





